With the advancement of information technology, China's digital transformation has brought about the rapid development of new technologies such as big data, IoT, public cloud and artificial intelligence. However, the accompanying security problem has been becoming more and more serious. On the one hand, with the popularity of cloud computing and micro-service mode, the business model we are facing has been becoming more and more complex. On the other hand, with the introduction of a series of compliance policies, such as domestic level protection 2.0, network security law and EU GDPR, the data review has been becoming more and more stringent. In addition, the pattern of network security threats has also undergone tremendous changes. Security personnel have to face a lower attack threshold, a wider attack area and more attack methods. With the low cost, module and weapon tendency of attack tools, network attacks are no longer the patent of hackers. Any person or group with ulterior motives can use these tools to penetrate or attack enterprises, resulting in huge digital assets and economic losses. At the same time, excessive security risks will greatly reduce the company's market value, and even threaten the survival of the company. Even a tiny potential risk can put the company's brand image, customers' privacy information and intellectual property at risk.
In recent years, network security incidents break out one after another, and enterprises frequently suffer from blackmail software, resulting in business suspension and data loss, and they have to pay a huge ransom for decryption; database defense line has been broken through; hotel check-in records, credit card numbers, personal medical privacy and other social information have been sold everywhere via illegal networks; continuous big-traffic DDoS attacks continue to paralyze the normal operations of websites. These security threats are causing huge losses to enterprises. At the same time, the security of cloud computing business is also a thorny problem faced by many enterprises. The mixed environment in which hardware and software coexist has also posed higher requirements for application security. Based on years of experience in security business and security incident response, ECCOM Network has launched a new "ECCOM Big Security 2.0" solution, which comprehensively protects the security and availability of enterprise business and data.
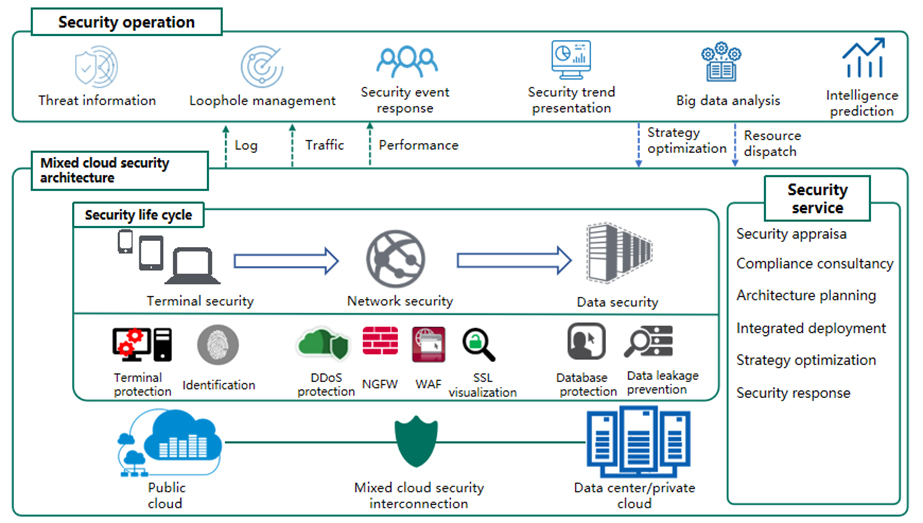
“ECCOM Big Security 2.0” Solution is to meet the ultimate goal of enterprise security policy, design and improve user information systems in such aspects as terminal security, network security, data security, cloud security and security service operation, continuously strengthen the visualization of internal information environment and enhance the level of overall security management and maintenance with the help of ECCOM's rich experience in project implementation and system integration and through the cycle of security assessment, architecture planning, integrated deployment and implementation and optimal management, so that the risk of existing security threats to information assets of network and application systems can be reduced to an acceptable range.
Terminal - network - data constitutes the basic life cycle of enterprise information business. In the aspect of terminal security, in order to better deal with unknown threats, the solution suggests adopting a next generation scheme of terminal protection which combines machine learning, big data behavior analysis and sandbox technology to effectively protect against zero-day attacks. At the network level, ECCOM Network can help enterprises to cope with DDoS attacks, APT attacks and Web application attacks, give full consideration to the increasing encrypted traffic, and carry out intelligent analysis and in-depth detection. The security of business data system, as the gathering point of information, is very important. The solution suggests deploying a system based on database protocol analysis and user behavior analysis (UEBA) to help enterprises detect various data violations, and avoid information disclosure.
On the other hand, cloud and big data analysis, as hot areas in recent years, have had important impacts on the digital transformation of enterprises. The information security solution of ECCOM Network can extend the security protection of enterprises to public and private clouds, so that the security of business assets in the cloud can reach the same level as that in the data center. At the same time, with the help of big data analysis, the solution collects threat information and vulnerability information, analyzes and presents the overall security threats of enterprises as a whole, carries out security emergency responses for key business, correctly handles security threats, and achieves intellectualization and visualization of information security through a complete security operation system.
“ECCOM Big Security 2.0” Solution is a complete system. The architecture of the solution covers all aspects of information system, and provides solutions and steps for the construction of network information security of ECCOM Network. The solution applies advanced technical means and management measures in the field of information security, guarantees users' network information security in an all-round way, and escorts the healthy development of enterprises.
Contact Us
Questions about which solutions are right for your organization? We can help!
REQUEST DEMO


